You can input this program into the editor, or use a special input device, such as a keyboard ormouse. Once GCC has created a program, you can use the gcc command to link it into a program. This will add the correct library functions to the program. You can use the -Wl, -Wl, and -Wno options to tell GCC to emit warnings, and -c to run the code. The gcc command also allows you to run tests. This is done by specifying -T tests and the name of the site that you want to run the tests on. The homeland division could also be relyant on individual employees for information and support, which could lead to confusion if one number fails to function properly. When all is said and done, the process of choosing the perfect card holder will be simple and efficient. By following these simple tips, you can create a design that is both stylish and functional. Not everyone agrees with this security measure, but it's something we've got to keep in mind in the event that something happens to one of our cards or documents. This is likely to be a more automated process, as the cards will likely be available for purchase through a series of websites.
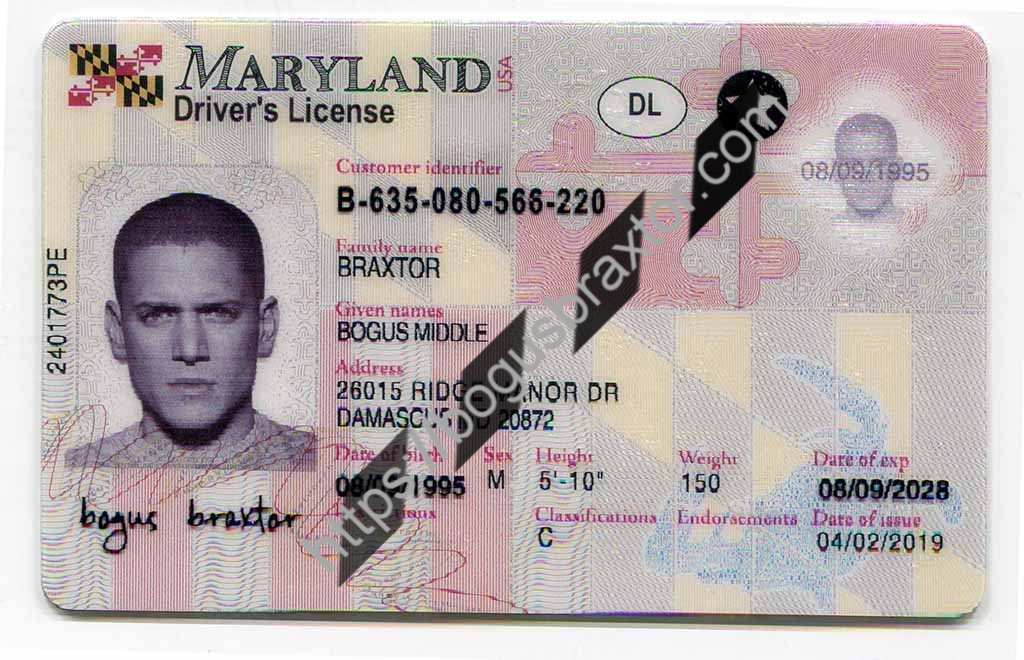







 What Address Should I Use For A Fake Id
What Address Should I Use For A Fake Id